Pritesh Prajapati
@PriteshPrajapati - 55 本の動画
チャンネル登録者数 2600人
WARNING: "Please note, these videos are just for educational purposes, For every attempt to illegally hack into third-party system(s), you might be punished ...
最近の動画
 1:31
1:31
AES Mix Column Example with GF(2^8) Polynomial Method
 32:01
32:01
NAT, Bridged and Internal Networking in VirtualBox
 7:20
7:20
#PNP CryptoCalc-App-Demo
 1:18:47
1:18:47
2. Classical Encryption Techniques
 1:07:28
1:07:28
11. RSA Summary and Examples || Open SSL
 1:10:00
1:10:00
10. Public Key Crypto with RSA
 37:06
37:06
12. Attacks on Diffie Hellman Key Exchange
 1:08:20
1:08:20
9. Fermat's Theorem, Euler's Theorem and Discrete Logs
 1:09:39
1:09:39
8. Divisibility, Primes and Modular Arithmetic
 58:54
58:54
Bitcoin (Part 2)
 1:40:31
1:40:31
Bitcoin (Part 1)
 57:57
57:57
7. Pseudo Random Number Generators
 1:14:33
1:14:33
Internet Privacy with Proxies, VPNs and Tor (Part 2)
 1:31:01
1:31:01
Internet Privacy with Proxies, VPNs and Tor (Part 1)
 1:01:07
1:01:07
6. Block Cipher Modes of Operation
 2:58
2:58
FileZilla for File Transfer with Linux in VirtualBox
 4:49
4:49
Best Ever Google Doodle | Let's Play ICC Champions Trophy 2017 | 200 Runs | Double Century
 7:17
7:17
Cyber Law || Information Technology Act 2000 || Cyber Crimes | Cyber Frauds
 11:02
11:02
Interpersonal Issues Online | Cyber Security
 10:03
10:03
Reading URLs | Cyber Security
 14:57
14:57
Social Engineering | Cyber Security
 10:01
10:01
Social Media and Privacy | Cyber Security
 10:42
10:42
Social Media and Security | Cyber Security
 34:03
34:03
Wireless Network | Security Threats | Public Networks | Administering Wireless | Cyber Security
 46:28
46:28
How Web Browsing works? | Safely Navigating the Web | Online Shopping | Cyber Security
 40:47
40:47
Malware, Functions of Malware, Sources of Malware, Layers of Defense Against Malware |Cyber Security
 22:58
22:58
How Email Works & Email Security | Cyber Security
 29:14
29:14
Passwords | Hash Function | Common Password Threats | Cyber Security
 13:45
13:45
Creating, Managing Strong Passwords | Cyber Security
 33:30
33:30
Demystifying the Internet || About Internet || Cyber Security
 21:12
21:12
Demystifying Computers || About Computers || Cyber Security
 15:58
15:58
Cyber Security Terminology
 6:40
6:40
Why Study Cyber Security?
 11:00
11:00
#PNP #13 #SQL Injection Attack in Virtual Network
 49:05
49:05
Introduction to Firewalls
 44:34
44:34
5. Simplified Data Encryption Standard (SDES) | Simplified DES | With an Example
 1:09:21
1:09:21
4.Transposition Ciphers and Steganography
 1:13:49
1:13:49
3. Caesar Cipher
 34:02
34:02
#PNP #12 #Wireshark - Packet Capture - Tutorial
 50:33
50:33
1. Introduction to Security
 3:41
3:41
What is a Blog?
 9:47
9:47
CyberSecurity Definitions
 9:54
9:54
Free Step by Step Guide for e-Filing Income Tax Return (ITR) Online (India)
 1:17
1:17
Learn Hill Cipher in 76 Seconds only || With 3x3 Matrix Multiplicative Inverse Example in Mod 26
 11:15
11:15
Hill Cipher || With 3x3 Matrix Multiplicative Inverse Example in Mod 26
 1:48
1:48
Known Plaintext Attack || Chosen Plaintext Attack
 4:00
4:00
Caesar Cipher || Shift Cipher || Additive Cipher
 1:08
1:08
What is Penetration Testing?
 16:26
16:26
Public Key Cryptography: RSA Algorithm
 7:30
7:30
How to Secure WordPress with Better WP Security Plugin ?
 6:27
6:27
Why Physical Security and Password are Important ?
 3:55
3:55
Why is Information Security Important ?
 11:43
11:43
#PNP #10 #Parrot Security OS 2.1 Installation Steps in Virtual Box - Hacking OS - Tutorial
 4:19
4:19
#PNP #01 #Kali Linux 2.0 Installation Steps in Virtual Box - Hacking OS - Tutorial
 2:59
2:59
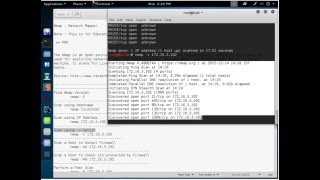
#PNP #06 #Nmap - Network Mapper - Kali Linux - Hacking OS - Tutorial
人気の動画
 44:34
44:34
5. Simplified Data Encryption Standard (SDES) | Simplified DES | With an Example
4.8万 回視聴 - 8 年前
 1:17
1:17
Learn Hill Cipher in 76 Seconds only || With 3x3 Matrix Multiplicative Inverse Example in Mod 26
2.2万 回視聴 - 8 年前
 4:19
4:19
#PNP #01 #Kali Linux 2.0 Installation Steps in Virtual Box - Hacking OS - Tutorial
5321 回視聴 - 9 年前